
Blog / There’s Admin and there’s Admin – Domain Administrators vs Local Administrators
User Authentication is a big deal in any organization. In most outfits, this is done through Windows. They deal with their users by making use of an Active Directory Server.
The reason why I brought this up is because just the other day I was asked about the difference between a user that is a Domain Administrator and one who is simply a Local Administrator. My response was that you need to tightly control them both, but when you get right down to it, being local is more powerful than being a domain one.
This is a tricky topic to try and keep simple, but I will certainly do my best. The easiest way to explain the difference between a Local Admin and a Domain Admin is to summarize the purpose of both types of accounts.
So, consider a Domain Administrator: A Domain Administrator is basically a user authorized to make changes to global policies that impact all the computers and users connected to that Active Directory organization. They have permission to go anywhere and do anything, with the limitation being that they must remain within that specific outfit.
Now consider a Local Administrator: A Local Admin has the permission to do anything but is restricted to one machine.
On the surface it would seem like the Domain Administrator had more power, which is not really the case. You see, the limitation is that the Domain Administrator cannot do anything outside of the domain. A Local Administrator is already outside the domain and has the full power to do anything desired on the location machine, which IS PART of the domain. They can decode any part of the machine they want and even remove sections of it from the control of the domain.
The final proof I can offer that a Local Administrator trumps a Domain Administrator is that you can easily leverage Local Admin privileges, in order to obtain Domain Administrator access. When I say “easily”, I am not exaggerating. While it requires a high level of skill and understanding to pull-off, once you have that level of skill, it is not particularly complicated. You can find numerous YouTube videos that walk you through and explain the process in just a few minutes.
There is no such thing as an Administrator Level of account that should not be monitored and restricted. Also, there is nothing that anyone does in their day-to-day activity that requires such level of access all the time, and I do mean “anyone.” This even applies to people in a position like the Techs who work at TRINUS, whose job it is to help customers and trouble-shoot problems. A lot of the things they do have no need of Administrator privileges, although many things certainly do.
An organization of any sort has the obligation to protect itself, to the best of its abilities. An easy way of doing so, is through the restriction and tight control of Admin access. This is not limited to Windows-based accounts. It applies to things like Databases (since they contain important information), Firewalls (which protect your outfits), Wireless Access points (provide wireless access to your network), & more.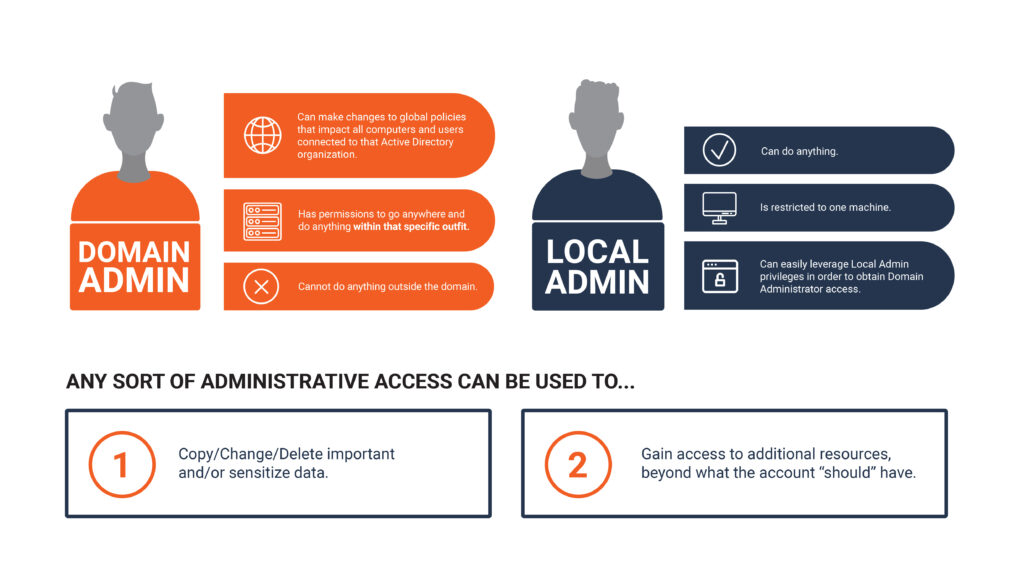
The fact is that any sort of Administrative Access can be used for at least one of two things:
1.) Copy/Change/Delete important and/or sensitize data // 2.) Gain access to additional resources, beyond what the account “should” have
That is why it is so important to restrict who has access to those sorts of accounts and keep an eye on the activity.
Any questions about Restricting Administrator Accounts? If so, please reach out to your TRINUS Account Manager for stress-free IT.
By Kind Courtesy of Your Friendly Neighbourhood Cyber-Man.

















