Blog / Segregation! – Socially-despised Term has New Meaning when Applied to Networks
The word Segregation has a bad connotation – and rightfully so. The practice of restricting a person’s rights and privileges in society, based on skin colour, faith or ethnicity, has become unacceptable in our Western culture, even though it’s still practiced in some isolated areas. Segregation may still be around, but we hear the word a lot less than we used to. Karl Buckley – our Cyber Security Supervisor – wrote an interesting article on Network Segregation that I thought I would share with you. It speaks about the separation needed between parts of your network, to enhance Security. Segregation is a good thing in this case:
Another day another Newsletter, but will it be a new message? Not today. Today it’ll be something I’ve talked about before, but with some new justification to go with it, rather than just being simple advice.
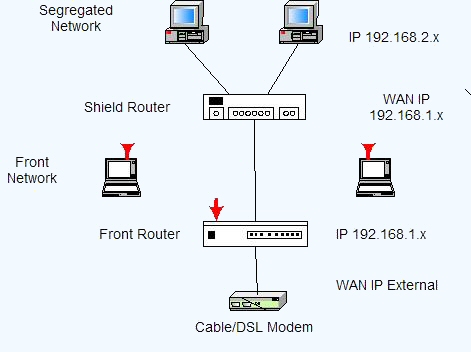
Network Segregation
The idea is simple, keep you network devices separated, based on their purpose and type.
Now for the all-important question, “Why is Network Segregation useful?” Well, I could say Security, but these Newsletters’ point is to prove a point, so here goes:
You gain Security by preventing people from being able to do something like this.
To summarize the article, Google didn’t segregate their network. This meant the hardware controlling their doors was accessible from normal PCs. One of their employees got a bit bored and poked around. They found they were able to manipulate the doors (open them, close them, prevent them from opening, etc.) Now then, the employee was just curious, and they reported all the vulnerabilities they found. Think about what sort of damage could have been done by someone intending harm. The lack of segregation could have enabled an attacker to obtain free access to the entire facility! It’s also worth noting that the employee found their manipulation left no traces.
Segregation is also recommended from just about everyone, when it comes to adding IoT (Internet of Things) devices to organizations.
Generally speaking, segregating your network-capable devices doesn’t involve additional costs in hardware (although it might.) It does involve some additional time and planning (best done in the beginning.) Doing proper segregation when you design a computer network, is certainly a lot easier than trying to do it after the fact.
Now you may remember that I covered Network Segregation in a previous Newsletter.
So why bring it up again? Well, as you may or may not know, TRINUS has been offering (and doing) Network Security Assessments at various Customer locations and networks for the past few months.
So what?
Well, some level of additional Network Segregation has been a recommendation … every … single … time.
As a network design idea, Network Segregation was old news back when I went to school about 2 decades ago. These days, it’s also a recommendation from any computer Security-related organization. Despite all this, the point doesn’t seem to be getting across.
Something that goes hand-in-hand with Network Segregation is known as “Air gaping” your networks. The term means exactly what the words say. When you have multiple networks, you have “a gap of air” between them. Simply put, this means you don’t share hardware between different networks. Often what happens with Network Segregation is that companies will use a single switch in various places, and then logically separate the traffic on different computer networks, so they have no access to each other. They achieve logical separation of traffic, but not physical separation.
This is fine, until you run into a scenario when an attack on one network causes a shared switch to crash… which in turn takes out the traffic of any other network connected to it. It also means there’s the risk of that device being compromised and allowing an attacker to jump into another network.
From a pure Security standpoint, separate hardware for each network is the ideal way to go. If there’s no link between networks, then a bad actor is effectively limited in the scope of their attack. However, this also increases costs. Security is always about the Cost-Benefit analysis and finding acceptable amounts of risk.
- What Security will be gained by doing <something>?
- What is the risk of not doing <something>?
- How much will doing this cost?
- If we don’t do this and something goes wrong because of it, how much will that cost?
- How likely is that to occur?
Depending on your organization, a certain level of Network Segregation may be required. PCI regulations demand ATM’s and Card Readers (and their traffic) are not accessible from any other network. This means those devices must be segregated. Failure to do so could result in fines and temporary (or permanent) loss of your privileges to use those Services!
If you have any questions about Network Segregation, you can always reach out to your TRINUS Account Manager for some stress-free IT Network Security Assessments.
Thanks,
Dave White
TRINUS
stress-free IT

















