Blog / If a Picture Paints 1000 Words, then Why Not Pay 1000 Dollars for it?
A little while ago, the “Black Hat Hacker“ Convention took place in Las Vegas. This is a yearly event that hosts both official and unofficial Security Researchers and allows them to showcase and talk about their latest hacking methods.
Normally a “Black Hat Hacker” would be the one that performs illegal activities vs a “White Hat Hacker“, who operates within the rules of the law. Everyone in Security will agree that limiting yourself to operating within the law, limits the kind of vulnerabilities you can find. Let’s face it: The bad guys won’t limit themselves like this.
This is where the “Black Hat Hacker Convention” comes in. It’s not that the people giving talks are illegal hackers. It’s just that the topics which Presenters cover don’t have the limits you would normally see with legal hacks.
I didn’t attend, but there are plenty of news articles floating around about the various vulnerabilities and hacks that were disclosed. It’s not uncommon to see hacks that involve closed or proprietary hardware, such as ATM’s. These are devices that people aren’t normally allowed to perform external testing on. One hack involved installing DOOM on an ATM.
Some of the talks and discussions are proof of concepts (POC.) That means that they haven’t necessarily done it, but the hack is theoretically possible. These sorts of chats are great for pointing-out possible weaknesses and room for Security improvement.
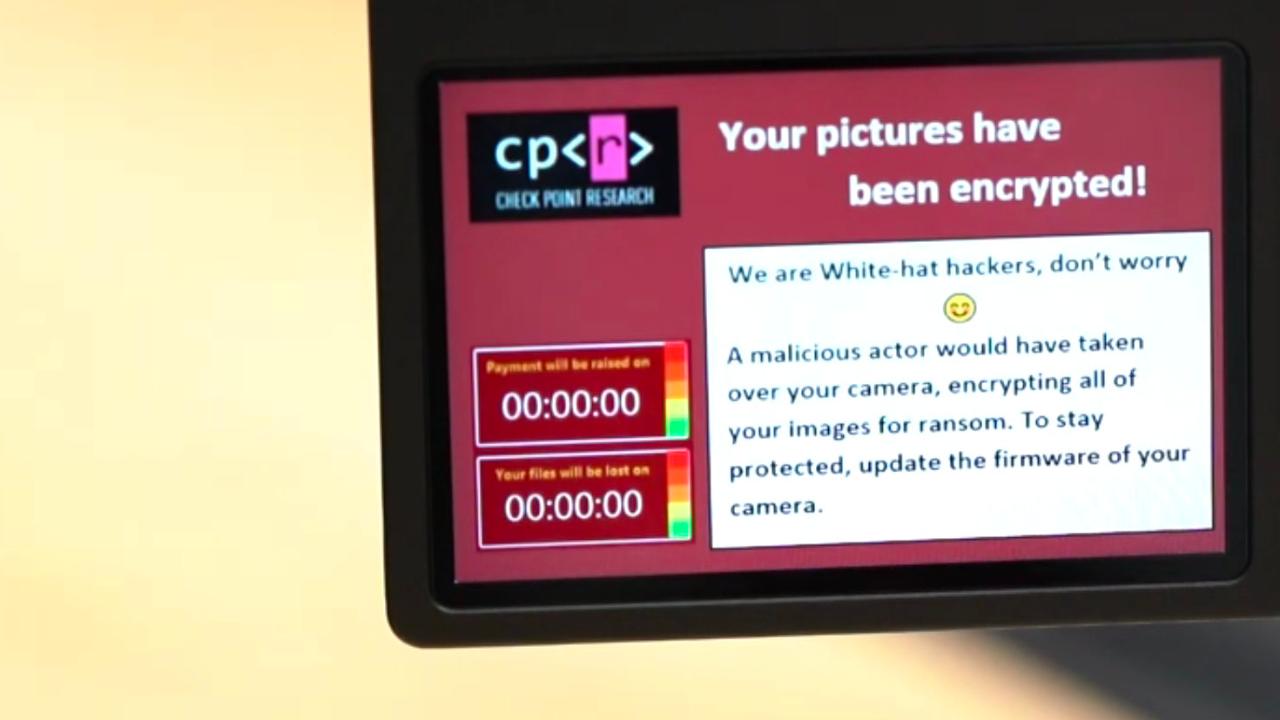
Anyway, enough of all that. One article caught my eye, which I thought was worth talking about in a newsletter: Someone managed to install Ransomware on a digital camera!
This wasn’t a proof of concept. They bought a camera and figured-out a way to install Ransomware. What was more alarming is that they did it without any sort of user interaction or physical access to the device.
The camera they selected had a WiFi option. Its intended use was to make it easy to connect from a computer and copy-off the pictures. Now obviously the attacker did not make use of this for the intended purpose. It was interesting in several ways:
First, how much could you expect to get for Ransomware on a camera?
At first, I laughed at this. After a moment, I sat back and thought about the sort of data you’d find on a digital camera. Many pictures are very important to people, because they have a lot of memories wrapped-up in them. Also, if you think about the very expensive digital cameras, who buys them? The primary market for the highly expensive cameras isn’t hobbyists; it’s professionals. Someone’s livelihood and business could be at stake. Also, those cameras aren’t cheap in the first place, so you could reasonably ask for several thousands of dollars and still have a good chance of being paid.
Second, if they could do it with a camera, could they do it with anything else?
The Camera in question had WiFi and Bluetooth for various wireless purposes. The attack in question made use of the default WiFi setup. The attacker connected to the network using the default information and then connected to the camera to do their dirty work. This default information is easy to find, because it’s published, publicly. Simply look up the manual for the device, and you’ll almost always find a PDF version somewhere on the Internet.
There are plenty of devices that have the same sort of setup as this camera did. A common one these days is a printer. Many printers have a wireless setup that’s intended to make it easy to print from your Smart phone or Tablet.
One habit I have is that from time to time I pull-out my cellphone, simply to glance at the WiFi networks that are nearby. Not to connect to any of them; simply to see what’s around. The number of defaults I see is truly disheartening.
Now you may think that the reason I see this so often is because I live in the small town of Spirit River, about an hour north of Grande Prairie. The truth is I see this everywhere. The last time I was in Vancouver International Airport, I noticed at least 3 Epson printers and a TELUS Internet connection. I identified them all simply by the default name of the WiFi. I may also have performed a minor hack by printing-out several copies of a page saying: “Please Secure your printer”, but I consider that a service, since I didn’t have the time to investigate which company owned that printer.
Ransomware is a thing. The truth of the matter is that it is not going to go away anytime soon. The reason being that for relatively little effort, a criminal can be reasonably sure to expect a payout. This means that spreading Ransomware is profitable. Until such time as there is no profit in it, Ransomware will continue to be a persistent, evolving threat.
If you have any questions about Ransomware, you can always reach out to your TRINUS Account Manager for some stress-free IT.
By Kind Courtesy of Your Friendly Neighbourhood Cyberman.

















